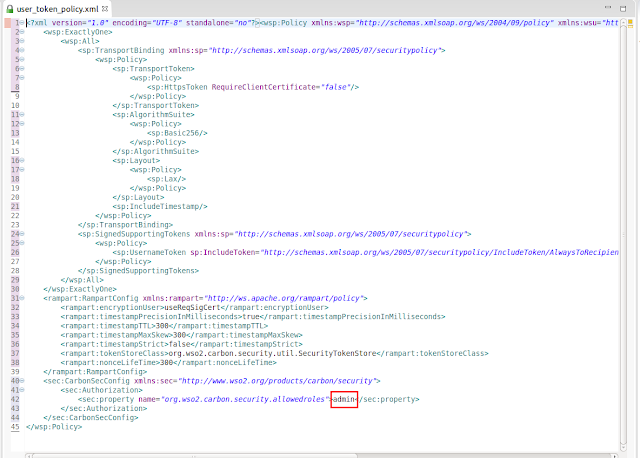
Step 1 Create a trusted connection in informix DB
For this you will need the ip of the connection that will try to connect to the DB and the user name of that respective connection. So in my example the details is as follows,
- IP - 192.168.1.5
- User - Simple
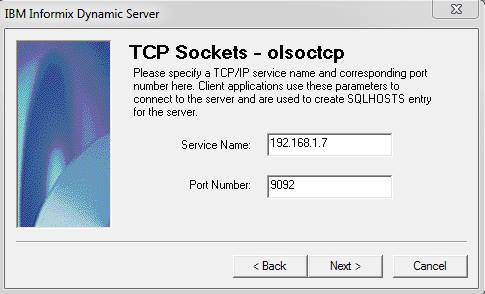
Launch a server instance and access the instance via "dbaccess". Navigate to "Query - Language" then you will be asked for a database to select. Select one of your desired databases and press "Enter". Now click on "New", you will be taken to the "Query Editor" (Refer below pic)
Now first grant permission to the user to enable him to grant privileges to create trusted connections for that you can use the following query,
1) GRANT DBSECADM TO {INFORMIX_USER};
Now that we granted the user permission to create trusted connections now lets look at the sample query that will enable informix to identify a user who is trying to connect to the DB without providing a username and password in the connection string.
2 ) CREATE TRUSTED CONTEXT tcx1 USER Sample ATTRIBUTES (ADDRESS '192.168.1.5') ENABLE;
3) GRANT CONNECT TO Sample;
In query 2 "Sample" is the username that I am going to provide permission to connect without providing a username and password. The address 192.168.1.5 is the address that the user will try to connect to the DB. Query 3 is to grant permission regarding to connection for the server. After executing the above two queries we have now configured user "Sample" to connect without username and password.
Step 2 Connect and test the trusted connection without credentials
I will be using DBeaver as the DB client to test this connection. DBeaver is a universal db connection tool which can be downloaded from here.
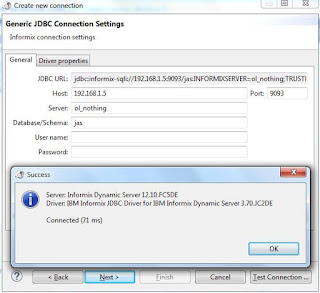
Now run the DBeaver client and create a new informix connection and provide the connection details as below.
jdbc:informix-sqli://192.168.1.5:9093/{DB_NAME}:INFORMIXSERVER={SERVER_NAME};TRUSTED_CONTEXT=TRUE
Now test the connection without providing a user name and password. You will be successfully connected to the DB(refer below pic).